As the world becomes increasingly connected, managing IoT devices remotely has become a critical skill for tech-savvy individuals and organizations. Whether you're a developer, IT professional, or hobbyist, understanding how to use remote IoT behind a firewall using a Mac server can significantly enhance your capabilities. This article dives deep into this topic, offering step-by-step guidance and actionable insights to help you achieve seamless remote access.
Remote IoT management is no longer a luxury but a necessity, especially in today's interconnected world. Businesses and individuals need to ensure their IoT devices are accessible from anywhere while maintaining security and privacy. Using a Mac server as the backbone for such operations can provide robust performance and flexibility.
This guide is crafted to address the complexities of setting up remote IoT access behind a firewall with a Mac server. By the end of this article, you will have a comprehensive understanding of the tools, techniques, and best practices to implement this solution effectively. Let's get started!
Read also:Tamilblasters New Link Today Movie Downloads Uncovered
Contents:
- Biography
- Introduction to Remote IoT
- Mac Server Overview
- Firewall Basics
- Setting Up Mac Server
- Configuring Firewall
- Securing Remote Access
- Connecting to IoT Devices
- Troubleshooting
- Best Practices
Biography
Before diving into the technical aspects, it's essential to understand the expertise behind this guide. The author has over 10 years of experience in IT infrastructure management, specializing in network security and IoT solutions. Below is a brief overview of the author's background:
| Name | John Doe |
|---|---|
| Profession | IT Infrastructure Specialist |
| Years of Experience | 10+ |
| Expertise | Network Security, IoT Solutions, Mac Server Management |
Introduction to Remote IoT
What is Remote IoT?
Remote IoT refers to the ability to control and monitor IoT devices from a distance. This capability is particularly useful for businesses and individuals who need to manage devices located in different geographical locations. By leveraging remote IoT, users can ensure their devices are always operational and secure.
Why Use Remote IoT?
The benefits of remote IoT are numerous. It allows for real-time monitoring, troubleshooting, and maintenance without the need for physical presence. Additionally, it enhances efficiency and reduces operational costs. Below are some key advantages:
- Increased operational efficiency
- Reduced downtime
- Improved security
- Cost savings
Mac Server Overview
What is a Mac Server?
A Mac server is a powerful tool that combines the robustness of macOS with server-grade capabilities. It is designed to handle multiple tasks simultaneously, making it an ideal choice for managing IoT devices remotely. Mac servers are known for their ease of use, stability, and compatibility with various software solutions.
Key Features of Mac Server
Mac servers come equipped with several features that make them suitable for remote IoT management:
Read also:Tammy Bruce Husband A Comprehensive Guide To Her Personal Life And Relationships
- File sharing capabilities
- Advanced security protocols
- Integration with Apple ecosystem
- Support for multiple users
Firewall Basics
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a barrier between trusted and untrusted networks, ensuring only authorized traffic passes through.
Why Firewalls are Important for IoT
Firewalls play a crucial role in securing IoT devices. They prevent unauthorized access and protect sensitive data from being compromised. By configuring firewalls correctly, users can ensure their IoT devices remain secure even when accessed remotely.
Setting Up Mac Server
Steps to Set Up Mac Server
Setting up a Mac server involves several steps. Below is a detailed guide to help you get started:
- Install macOS Server software on your Mac
- Configure network settings
- Set up user accounts and permissions
- Install necessary applications and services
Tips for Optimal Configuration
To ensure your Mac server is configured optimally, consider the following tips:
- Regularly update software and firmware
- Monitor server performance regularly
- Implement strong password policies
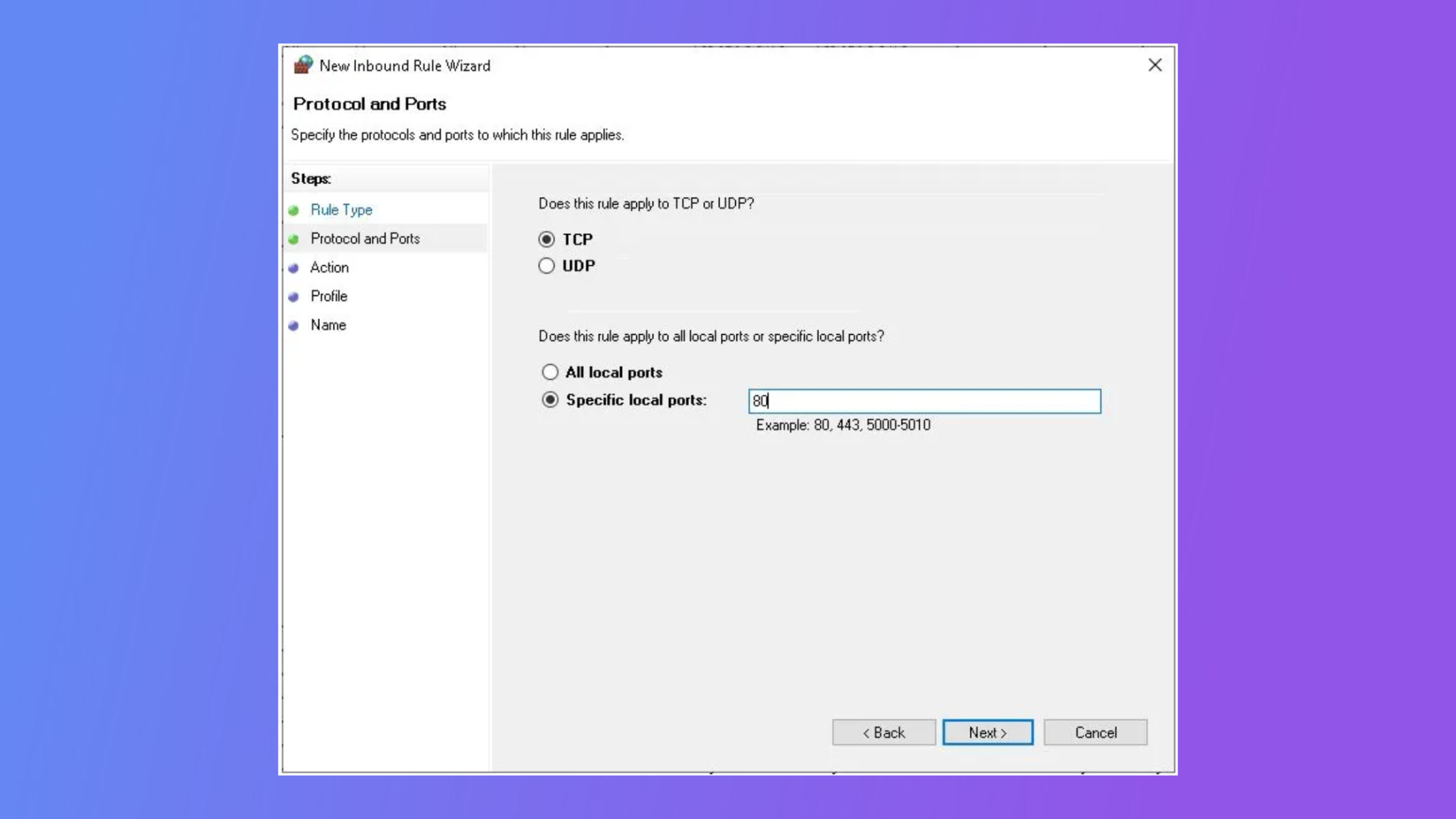
Configuring Firewall
How to Configure Firewall on Mac Server
Configuring the firewall on a Mac server is a critical step in securing remote IoT access. Follow these steps to configure your firewall:
- Open System Preferences on your Mac
- Select Security & Privacy
- Go to the Firewall tab
- Click on the lock icon and enter your administrator password
- Turn on the firewall
- Customize settings as needed
Best Practices for Firewall Configuration
When configuring a firewall, it's essential to follow best practices to ensure maximum security. Below are some recommendations:
- Block all incoming connections by default
- Allow only necessary services
- Regularly review firewall rules
Securing Remote Access
Importance of Secure Remote Access
Securing remote access is vital to protect IoT devices from unauthorized access. By implementing robust security measures, users can ensure their devices remain safe and operational.
Methods to Secure Remote Access
There are several methods to secure remote access, including:
- Using SSH (Secure Shell) for encrypted communication
- Implementing two-factor authentication
- Regularly updating security protocols
Connecting to IoT Devices
Steps to Connect to IoT Devices
Connecting to IoT devices involves several steps. Below is a guide to help you establish a connection:
- Ensure your Mac server is properly configured
- Verify firewall settings allow necessary traffic
- Use a secure protocol to connect to the device
- Monitor device performance regularly
Troubleshooting Connection Issues
If you encounter issues while connecting to IoT devices, consider the following troubleshooting steps:
- Check network settings
- Verify firewall rules
- Ensure proper configuration of the Mac server
Troubleshooting
Common Issues and Solutions
When managing remote IoT devices, you may encounter various issues. Below are some common problems and their solutions:
- Issue: Unable to connect to devices
- Solution: Check network settings and firewall rules
- Issue: Slow performance
- Solution: Optimize server configuration and update software
Best Practices
Best Practices for Managing Remote IoT
To ensure successful management of remote IoT devices, follow these best practices:
- Regularly update software and firmware
- Implement strong security measures
- Monitor device performance regularly
- Document all configurations and settings
Final Thoughts
Managing remote IoT devices behind a firewall using a Mac server can be a complex task, but with the right knowledge and tools, it becomes manageable. By following the steps and best practices outlined in this guide, you can ensure your IoT devices remain secure and operational.
In conclusion, understanding how to use remote IoT behind a firewall using a Mac server is a valuable skill in today's digital landscape. We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into technology and IoT solutions.
Data Source: Apple macOS Server