As technology advances, the demand for remote IoT solutions continues to grow exponentially. However, one of the most pressing challenges in deploying IoT devices is ensuring secure communication when they are located behind firewalls. In this article, we will explore how to use remote IoT behind a firewall using Mac Server as an example. This guide is perfect for tech enthusiasts, network administrators, and anyone interested in secure IoT implementation.
Whether you're managing a smart home setup or a large-scale industrial IoT deployment, understanding how to configure your devices for remote access is crucial. Firewalls play a pivotal role in securing networks, but they can also block essential communication between IoT devices and external systems. This article will break down the process step by step, ensuring you have the knowledge to implement secure and reliable remote IoT setups.
Our focus will be on leveraging Mac Server as an example to demonstrate how to establish secure connections. By the end of this article, you'll have a comprehensive understanding of the technical aspects and best practices for implementing remote IoT solutions behind firewalls.
Read also:Mastering The Management Of Raspberry Pi Remotely A Comprehensive Guide
Understanding the Basics of Remote IoT
Before diving into the technical details, it's essential to grasp the fundamental concepts of remote IoT. IoT (Internet of Things) refers to the network of physical devices embedded with sensors, software, and connectivity capabilities, enabling them to collect and exchange data. When these devices are placed behind firewalls, accessing them remotely becomes a challenge that requires careful planning and execution.
What is Remote IoT?
Remote IoT involves configuring devices to allow secure access from outside the local network. This setup is crucial for monitoring, controlling, and managing IoT devices in real-time without compromising network security. By implementing robust solutions, you can ensure seamless communication while maintaining data privacy.
Why Use a Mac Server?
Mac Server offers a reliable platform for managing remote IoT deployments. Its compatibility with various protocols and ease of integration with third-party tools make it an ideal choice for this purpose. Additionally, Mac Server's built-in security features help protect sensitive data from unauthorized access.
Setting Up Mac Server for Remote IoT
Configuring Mac Server for remote IoT access requires a systematic approach. Below, we outline the key steps to ensure a successful setup:
Step 1: Install macOS Server
Begin by installing macOS Server on your Mac. This software provides essential tools for managing network services, including remote access capabilities. Follow the installation instructions carefully to avoid potential issues.
Step 2: Configure Network Settings
Adjust your network settings to allow secure communication between the Mac Server and IoT devices. This includes setting up static IP addresses, configuring DNS settings, and enabling necessary ports for data transfer.
Read also:X Hamster The Ultimate Guide To Understanding And Caring For Your Pet
Step 3: Secure the Server
Implement robust security measures to protect your Mac Server from cyber threats. This includes enabling firewalls, using strong passwords, and regularly updating the operating system and applications.
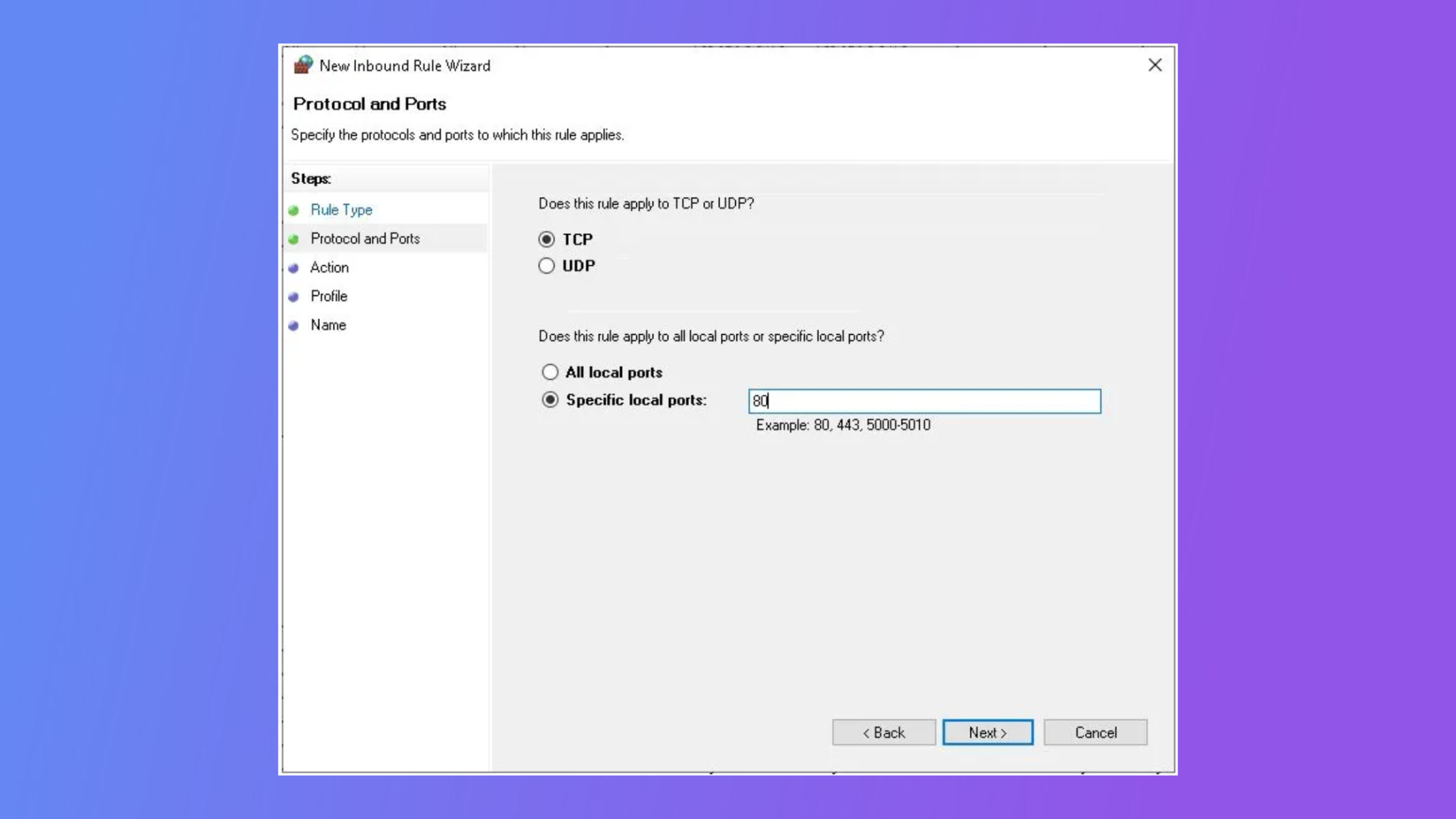
Implementing Firewall Rules
Firewalls are critical components in securing IoT deployments. Properly configuring firewall rules ensures that only authorized traffic can access your devices.
Key Firewall Considerations
- Identify necessary ports for IoT communication.
- Create rules to allow inbound and outbound traffic for specific IP addresses.
- Regularly review and update firewall settings to adapt to evolving security threats.
Using SSH for Secure Connections
SSH (Secure Shell) is a protocol that provides encrypted communication between devices. It's an excellent choice for securing remote IoT connections.
Setting Up SSH on Mac Server
Enable SSH on your Mac Server by navigating to the Sharing preferences in System Settings. Once enabled, you can connect to your server securely from remote locations using SSH clients like Terminal or PuTTY.
Implementing Port Forwarding
Port forwarding allows external devices to access internal network resources by directing incoming traffic to specific ports. This technique is particularly useful for remote IoT setups.
Steps to Configure Port Forwarding
- Access your router's configuration page.
- Locate the port forwarding settings and specify the desired port numbers.
- Map the ports to the IP address of your Mac Server.
Ensuring Data Security
Protecting sensitive data is paramount in remote IoT deployments. Employing encryption and authentication mechanisms can significantly enhance security.
Encryption Methods
Use encryption protocols such as TLS (Transport Layer Security) to secure data transmissions. This ensures that even if intercepted, the data remains unreadable to unauthorized parties.
Monitoring and Managing IoT Devices
Efficient monitoring and management are essential for maintaining optimal performance and security of your IoT devices.
Tools for Monitoring
Leverage tools like Home Assistant, Node-RED, or Grafana to monitor device status, analyze data, and receive alerts in real-time. These platforms integrate seamlessly with Mac Server, providing a comprehensive view of your IoT ecosystem.
Best Practices for Remote IoT Deployment
Adhering to best practices ensures a secure and efficient remote IoT setup. Below are some recommendations to consider:
- Regularly update firmware and software for all devices.
- Implement multi-factor authentication for added security.
- Document all configurations and settings for future reference.
Case Study: Mac Server in Action
To better illustrate the implementation process, let's explore a real-world example of using Mac Server for remote IoT access. In this case, a small business deployed IoT sensors to monitor environmental conditions in their warehouse. By configuring Mac Server with appropriate firewall rules and SSH connections, they achieved secure remote access to the sensors, enabling real-time monitoring and data analysis.
Troubleshooting Common Issues
Even with careful planning, issues may arise during the setup process. Below are some common problems and their solutions:
Connection Failures
If you encounter connection issues, verify that all necessary ports are open and correctly configured. Additionally, check the firewall settings to ensure they are not blocking the traffic.
Conclusion
In conclusion, using remote IoT behind a firewall with Mac Server as an example involves several key steps, including configuring network settings, implementing firewall rules, and ensuring data security. By following the guidelines outlined in this article, you can successfully deploy secure and efficient remote IoT solutions.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our website for more insights into technology and IoT solutions. Together, let's build a smarter and more connected world!
Table of Contents
- Understanding the Basics of Remote IoT
- Setting Up Mac Server for Remote IoT
- Implementing Firewall Rules
- Using SSH for Secure Connections
- Implementing Port Forwarding
- Ensuring Data Security
- Monitoring and Managing IoT Devices
- Best Practices for Remote IoT Deployment
- Case Study: Mac Server in Action
- Troubleshooting Common Issues